'Nothing secret left' — Ukraine hacks Russia's Tupolev bomber producer, source claims

Ukraine's military intelligence agency (HUR) has gained access to sensitive data of Russia's strategic aircraft manufacturer Tupolev, a source in HUR told the Kyiv Independent on June 4.
Tupolev, a Soviet-era aerospace firm now fully integrated into Russia's defense-industrial complex, has been under international sanctions since 2022 for its role in Russia's war against Ukraine.
Its bombers have been widely used to launch long-range cruise missiles against Ukrainian cities and infrastructure.
According to the source, HUR's cyber corps accessed over 4.4 gigabytes (GB) of internal data, including official correspondence, personnel files, home addresses, resumes, purchase records, and closed meeting minutes.
"The significance of the data obtained cannot be overestimated," the source said. "Now, in fact, there is nothing secret left in Tupolev's activities for Ukrainian intelligence."
The intelligence includes detailed information about engineers and staff responsible for maintaining Russia's strategic bombers, such as the Tu-95 and Tu-160, which form a key part of Russia's nuclear triad.
"In particular, we have obtained comprehensive information about individuals directly involved in servicing Russian strategic aviation," the source added. "The result will obviously be noticeable both on the ground and in the sky."
Ukrainian cyber operatives also replaced the Tupolev website's homepage with an image of an owl clutching a Russian aircraft, likely referencing HUR's insignia and cyber warfare skills.
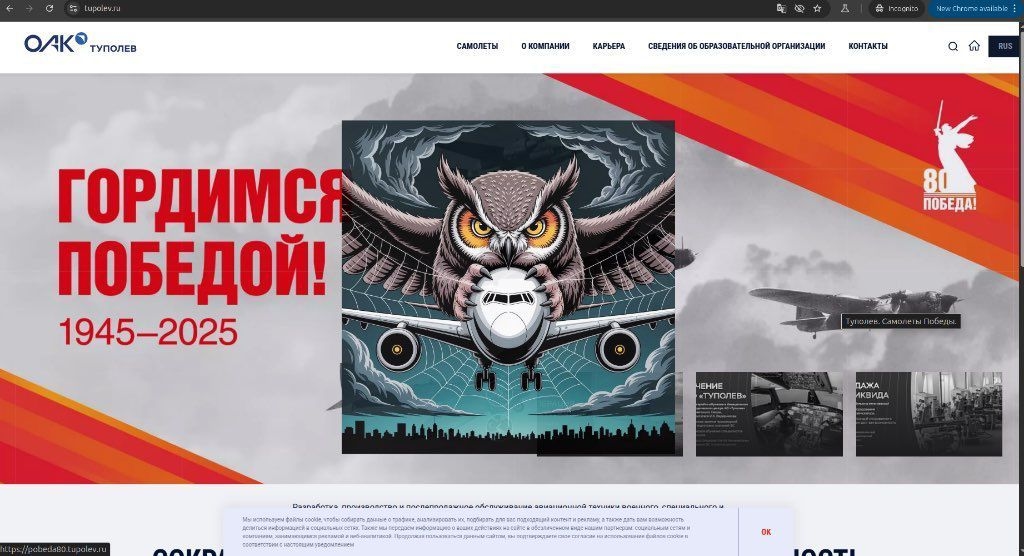
The breach comes days after the Security Service of Ukraine (SBU) crippled over a third of Russia's strategic bomber fleet in a major drone operation codenamed Spiderweb, which targeted four Russian air bases.
That attack reportedly damaged 41 aircraft, including Tu-95 and Tu-22M3 bombers, using drones launched from trucks hidden deep inside Russian territory.
The Kyiv Independent could not independently verify the number of aircraft reportedly hit by the SBU or some of the claims regarding the cyberattack.
The source shared excerpts of internal data obtained during the breach, including what appeared to be internal documents and personnel files of staff, as proof.
The combination of physical strikes on Russia's strategic aviation and now the exposure of its internal architecture marks a significant blow to Moscow's long-range aerial warfare.











